|
|
NEWS
Jun 3, 2009 21:40:47 GMT 4
Post by towhom on Jun 3, 2009 21:40:47 GMT 4
New research contributes to defense of Earth's technologiesLeicester scientists implement a new radar mode to create clearer picture of space weatherEurekAlert
Public Release: 3-Jun-2009www.eurekalert.org/pub_releases/2009-06/uol-nrc060309.phpUniversity of Leicester researchers have taken a step forward in helping to create a defence for earth's technologies –from the constant threat of space weather. They have implemented a "double pulse" radar-operating mode on two radars, which form part of a global network of ground based coherent scatter radars called SuperDARN (Super Dual Auroral Radar Network).These radars allow observations of space weather, which can have devastating impacts for technologies on earth. James Borderick, of the Radio and Space Plasma Physics group, within the Department of Physics and Astronomy, said: "Intense space weather events are triggered by the explosive release of energy stored in the Sun's magnetic fields. "A strong burst of electromagnetic energy reaches the Earth with the potential to disrupt many of our fundamental services, such as satellite and aviation operations, navigation, and electricity power grids. Telecommunications and information technology are likewise vulnerable to space weather. "All modern societies rely heavily on space systems, for communications and resource information (meteorological, navigation and remote sensing). There are high cost and high risks associated with the consequences of space weather events, as insurance companies recognise. "We have implemented a new "double pulse" radar-operating mode on the Radio Space Plasma Physics Group's Co-operative UK Twin Located Auroral Sounding System (CUTLASS) radars."The new sounding mode enhances our temporal resolution of plasma irregularities within the ionosphere. The resolution increase may help our understanding of coupling processes between the solar wind and the Earth's magnetosphere by allowing the observation of smaller scale phenomena with an unprecedented resolution. "Utilising our new radar mode and the vastness of ground based and space based instruments at our disposal, we are ever increasing our understanding of the countless phenomena associated with the Solar-Terrestrial interaction, and one day, may lead us to the accurate predictions of intense weather events- and an active defence." The research introduces the importance of utilising ground-based measurements of the near space environment in conjunction with spacecraft observations and then proceeds to explain the direct influences of space weather on our own technological systems. Mr Borderick will be presenting his doctoral research at the Festival of Postgraduate Research, which is taking place on Thursday 25th June in the Belvoir Suite, Charles Wilson Building between 11.30am and 1pm. Notice no mention was made of HAARP...any of the 47 or so HAARP arrays scattered around the world in a grid-like pattern.
That's what you are "defending" - not SuperDARN - the use of the HAARP technology.
|
|
|
|
NEWS
Jun 3, 2009 22:44:30 GMT 4
Post by locoaz2009 on Jun 3, 2009 22:44:30 GMT 4
Germany Blasts ‘Powers of the Fed’ By JOELLEN PERRY JUNE 3, 2009 Jim Sinclair’s Commentary There is no stopping the runaway locomotive heading directly at the US dollar. Now starts the parting of the ways between regions over who or why the disaster is upon us. German Chancellor Angela Merkel, in a rare public rebuke of central banks, suggested the European Central Bank and its counterparts in the U.S. and Britain have gone too far in fighting the financial crisis and may be laying the groundwork for another financial blowup. "I view with great skepticism the powers of the Fed, for example, and also how, within Europe, the Bank of England has carved out its own small line," Ms. Merkel said in a speech in Berlin. "We must return together to an independent central-bank policy and to a policy of reason, otherwise we will be in exactly the same situation in 10 years’ time." Ms. Merkel also said the ECB "bowed somewhat to international pressure" when it said last month it plans to buy €60 billion ($85 billion) in corporate bonds — a move that is modest in comparison to asset-buying by its counterparts, the U.S. Federal Reserve and Bank of England. Details are to be unveiled by the ECB’s president, Jean-Claude Trichet, Thursday. The public criticism is unusual — and not only because German politicians rarely talk harshly about central banks in public. When politicians around the world do criticize their central banks, they almost always gripe that they are too tightfisted. The conservative German leader’s comments came as Europe’s statistical agency reported that unemployment in the 16 countries that share the euro rose to 9.2% in April — the highest level since September 1999 and still below the 11.5% that the European Commission forecasts for 2010. jsmineset.com/LOCOAZ |
|
|
|
NEWS
Jun 3, 2009 22:48:35 GMT 4
Post by locoaz2009 on Jun 3, 2009 22:48:35 GMT 4
Global Warming Could Pose A Threat to NATO Jim Sinclair’s Commentary Of course it will. There is oil there. Published yesterday by Christopher Szabo According to news reports, those most affected by global warming live in the 50 least developed countries, but this could change. Recent moves by Russia could call into question the NATO alliance’s naval defenses in the Arctic Circle region. A new Russian military force, especially developed for arctic conditions, is past the planning stages, according to Jane’s Defence. The force, once deployed, would be equipped with: “Special ammunition, ammunition and transport” for the freezing Arctic conditions. In the wake of the first ice-free month of the Northwest Passage in September, 2007, and Russian claims to most of the High North region, based on it’s claim to the Lomonosov Shelf, which Russia regards as being part of its own exclusive economic zone of 200 nautical miles, the creation of the new military force seems somewhat sinister. Unlike the Antarctic, the Arctic has no treaty banning commercial exploitation of its resources and not only Russia, but also the U.S., Canada, Denmark, Norway, Sweden, Iceland and Finland have laid claims to the region. While NATO officials and analysts have stressed the peaceful nature of Russia’s new force, comparing it with Russian cooperation with the West in the Mediterranean and fighting pirates off Somalia, Russian behaviour has not always been that of a good neighbour, especially in areas it considers to be part of its exclusive sphere of influence, such as the former Soviet Union republics. Russia has brutally crushed a Chechen separatist movement as well as fighting a brief war against the former Soviet Republic of Georgia last November. jsmineset.com/LOCOAZ |
|
|
|
NEWS
Jun 3, 2009 22:51:19 GMT 4
Post by locoaz2009 on Jun 3, 2009 22:51:19 GMT 4
Schwarzenegger says day of reckoning is here Jim Sinclair’s Commentary It always starts on the West Coast, but certainly moves into all states in one degree or the other. Sacramento Business Journal - by Kathy Robertson Staff writer The state wallet is empty. The bank closed. Credit has dried up, Gov. Arnold Schwarzenegger told lawmakers in a special Tuesday morning address at the Capitol. “California’s day of reckoning is here,” he said. With no action, the state will run out of cash in 14 days. Three months after the state budget was approved, California faces a $24 billion deficit. Schwarzenegger has already proposed massive cuts to education, health care and prisons. Now he’s looking for structural reform to make government more efficient and stretch taxpayer dollars. He’s asked the State Board of Education, for example, to make textbooks available in digital formats — a move that could save millions. In 2004, the governor talked about blowing up boxes and consolidating agencies, but the initiatives never gained traction. jsmineset.com/LOCOAZ |
|
|
|
NEWS
Jun 4, 2009 4:10:08 GMT 4
Post by towhom on Jun 4, 2009 4:10:08 GMT 4
I, myself, am not a fan of QuickTime - however - here is (are) the fix(es) for the latest wormy Apple stuff...I'm still waiting for the latest DirectX patches from MicroSnot... ;DApple plugs gaping QuickTime security holesZDNet News & Blogs / Technology News
by Ryan Naraine
Posted: June 1st, 2009 @ 1:37 pmblogs.zdnet.com/security/?p=3479&tag=nl.e550Apple today released QuickTime 7.6.2 with fixes for a variety of security vulnerabilities, some of which could lead to arbitrary code execution attacks. The update, available for Mac OS X, Windows XP and Windows Vista, covers a total of 10 documented vulnerabilities that could be exploited via booby-trapped movie, video, image and audio files. Here are the details: - CVE-2009-0188: A memory corruption issue exists in QuickTime’s handling of Sorenson 3 video files. This may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0951: A heap buffer overflow exists in the handling of FLC compression files. Opening a maliciously crafted FLC compression file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0952: A buffer overflow may occur while processing a compressed PSD image. Opening a maliciously crafted compressed PSD file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0010: An integer underflow in QuickTime’s handling of PICT may result in a heap buffer overflow. Opening a maliciously crafted PICT file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0953: A heap buffer overflow exists in QuickTime’s handling of PICT images. Opening a maliciously crafted PICT file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0954: A heap buffer overflow exists in QuickTime’s handling of Clipping Region (CRGN) atom types in a movie file. Opening a maliciously crafted movie file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0185: A heap buffer overflow exists in the handling of MS ADPCM encoded audio data. Viewing a maliciously crafted movie file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0955: A sign extension issue exists in QuickTime’s handling of image description atoms. Opening a maliciously crafted Apple video file may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0956: An uninitialized memory access issue exists in QuickTime’s handling of movie files. Viewing a movie file with a zero user data atom size may lead to an unexpected application termination or arbitrary code execution.
- CVE-2009-0957: A heap buffer overflow exists in QuickTime’s handling of JP2 images. Viewing a maliciously crafted JP2 image may lead to an unexpected application termination or arbitrary code execution.
The update is available via the Software Update utility (Mac OS X) and Apple’s Windows Automatic Software Update tool (Windows). Alternatively, QuickTime 7.6.2 may be obtained from the QuickTime Downloads site.
|
|
|
|
NEWS
Jun 4, 2009 4:30:39 GMT 4
Post by towhom on Jun 4, 2009 4:30:39 GMT 4
Texas A&M researchers examine 'invading' bacteria in DNACall it advanced warfare on the most elemental of levelsEurekAlert
Public Release: 2-Jun-2009www.eurekalert.org/pub_releases/2009-06/tau-tar060209.phpResearchers at Texas A&M University's Artie McFerrin Department of Chemical Engineering have discovered how certain types of bacteria integrate the DNA that they have captured from invading enemies into their own genetic makeup to increase their chances of survival. To be more accurate, the genetic material isn't really captured as much as it is simply utilized after it's injected into the bacteria by an invading virus, says Professor Thomas K. Wood, who along with colleagues Xiaoxue Wang and Younghoon Kim has published the findings in Nature's 2009 International Society for Microbial Ecology Journal. Wood's findings shed light on a millions-of-years-old battle between bacteria and bacteria-eating viruses known as "phages." Locked in an epic struggle, the two life forms, Woods explains, are constantly developing new ways to win the war. One such approach undertaken by a phage is to attach to a bacterial cell and, using a syringe-like tail apparatus, inject its genetic material into the bacterial cell. Once inside, the phage replicates itself and eventually exits the cell to find new bacteria to infect. But as is the case with men, the best-laid plans of phages can also go astray. Examining E. coli bacteria, Wood found that the bacteria developed a means of not allowing the phage to replicate and leave the cell of its own volition. Once the phage was effectively "captured," the bacteria incorporated the phage's DNA material into its own chromosomes. This new diverse blend of genetic material, Wood says, has helped the bacteria not only overcome the phage but also flourish at a greater rate than similar bacteria that have not incorporated the phage DNA. "The bacteria are alive and doing well, and in fact the bacteria are doing better because it captured its enemy," Wood said. "Our research shows that if these bacteria didn't have this particular set of 25 genes that belonged to the old phage it wouldn't be able to grow as fast. If you removed the phage remnant, the bacteria grows five times slower on some carbon sources." This distinct advantage is helping scientists understand why bacteria carry about 10-20 percent of genes that aren't their own. Simply put, carrying the virus DNA allows bacteria to increase their chances of survival by producing diverse progeny – something Wood says is extremely important when the bacteria choose to move to a new environment through a process known as dispersal. Dispersal occurs, Woods says, when the bacterium can no longer glean the nutrients it needs from its surroundings or when other environmental conditions, such as temperature, have become unfavorable. Wood found that through an elaborate regulation method, the bacteria are able to retain the virus DNA or expel it. It's an interesting trade off, as retaining the virus DNA helps the bacteria grow faster but reduces its motility, which is needed when seeking out new environments, Wood explains. Further exploring this dynamic, Wood and his research group were able to link this regulation process to the formation of bacterial communities called biofilms. A biofilm, Wood says, is a protective, adhesive slime created by bacteria that have joined together to form a community and reap the benefits of a "strength-in-numbers" approach. Biofilms can grow on a variety of living and nonliving surfaces, including submerged rocks, food, teeth (as plaque) and biomedical implants such as knee and hip replacements. The National Institutes of Health estimate that about 90 percent of infections in humans are caused by biofilms, and the Centers for Disease Control estimate biofilm to be present in 65 percent of hospital-acquired (nosocomial) infections. Biofilms typically are the cause of fatal infections that develop post surgery. More commonly, they are the source of persistent ear infections among children. In addition to finding that biofilm formation relies heavily on virus genes present within the bacteria, Wood's research has shown the mechanism for how this takes place. A protein within the bacterium called Hha has the ability to control whether virus genes are kept within the bacterium or jettisoned. When Hha is basically "turned on," the bacteria expel the virus genes, opting for motility over the ability to form biofilms. Likewise, when Hha is not expressed, the bacteria move slower but grow biofilms at a much faster rate, Wood explains. It's a finding that could impact everything from health care to research into alternative fuel production. "If we can understand how biofilms are formed, we can begin to manipulate forming them where we want and getting them to not form where we don't want them," Wood says. "We have found a regulator – this Hha – that controls the genes related to biofilm formation. Now we can begin to envision ways to turn on that Hha gene if we want to get rid of biofilms, and that is what we are working on. That's the long-term goal – as engineers to make biofilms where we want them. "For example, if we want to remediate soil, we'd form a biofilm on the roots of plants, plant the tree, and wherever the tree root goes we clean the soil. That's a beneficial biofilm. If I want to make hydrogen with E. coli, I'll probably want to do it in a biofilm, so I would want to promote the growth of the biofilm. "We're one of the first labs in the world that has begun to not only try to understand how biofilms form but to control them." Contact: Thomas Wood at (979) 862-1588 or thomas.wood@che.tamu.edu or Ryan A. Garcia at (979) 845-9237 or ryan.garcia99@tamu.edu.
About research at Texas A&M University: As one of the world's leading research institutions, Texas A&M is in the vanguard in making significant contributions to the storehouse of knowledge, including that of science and technology. Research conducted at Texas A&M represents an annual investment of more than $582 million, which ranks third nationally for universities without a medical school, and underwrites approximately 3,500 sponsored projects. That research creates new knowledge that provides basic, fundamental and applied contributions resulting in many cases in economic benefits to the state, nation and world.
For more news about Texas A&M University, go to tamunews.tamu.edu.
|
|
|
|
NEWS
Jun 4, 2009 4:45:49 GMT 4
Post by towhom on Jun 4, 2009 4:45:49 GMT 4
Hydrogen Peroxide Marshals Immune SystemScienceDaily
June 3, 2009www.sciencedaily.com/releases/2009/06/090603131431.htmWhen you were a kid your mom poured it on your scraped finger to stave off infection. When you got older you might have even used it to bleach your hair. Now there's another possible function for this over-the-counter colorless liquid: your body might be using hydrogen peroxide as an envoy that marshals troops of healing cells to wounded tissue. Using the zebrafish as an animal model, researchers in the lab of Harvard Medical School professor of systems biology Timothy Mitchison and Dana Farber Cancer Institute professor Thomas Look have discovered that when the tail fins of these creatures are injured, a burst of hydrogen peroxide is released from the wound and into the surrounding tissue. Teams of rescue-working white blood cells respond to this chemical herald, crawl to the site of damage, and get to work. "We've known for quite some time that when the body is wounded, white blood cells show up, and it's really a spectacular piece of biology because these cells detect the wound at some distance," says Mitchison. "But we haven't known what they're responding to. We do know something about what summons white blood cells to areas that are chronically inflamed, but in the case of an isolated physical wound, we haven't really known what the signal is." These findings are reported in the June 4 issue of the journal Nature. Philipp Niethammer, a postdoc in Mitchison's lab, and Clemmens Grabber, a postdoc in Look's lab, initiated this research project with no interest in wound healing. Rather, they were studying a groups of molecules called reactive oxygen species, or ROS. These small oxygen-derived molecules, of which hydrogen peroxide is one, have the potential to be both helpful and hurtful. Niethammer and Grabber were simply curious to find ways to detect ROS molecules in an organism. To do this, they took a gene engineered to change color in the presence of hydrogen peroxide and inserted it into zebrafish embryos. Once the embryos entered the larvae stage after a few days, this synthetic gene spread throughout the entire body, essentially "wiring" the fish so that any discreet location in which hydrogen peroxide appears would glow. But how do you coax the fish to produce a reactive chemical like hydrogen peroxide in the first place? Since white blood cells have long been known to produce hydrogen peroxide, one obvious way to initiate chemical production would be to inflict a small wound onto the fish, and then, using microscopy, observe patterns of this chemical as white blood cells gathered around the wound. But much to the researchers surprise, they found that hydrogen peroxide immediately appeared at the wound site, prior to the arrival of any white blood cell, and quickly disseminated into neighboring tissue.
They repeated the experiment, this time in zebrafish where they'd disabled a protein that was previously discovered to produce hydrogen peroxide in the human thyroid gland. Not only did hydrogen peroxide not appear at the wound site, but white blood cells failed to respond to the injury."This was our real eureka! moment," says Niethammer. "We weren't too surprised that we could block hydrogen peroxide production through this technique, but what we didn't expect at all was that white blood cells wouldn't respond. This proved that the white blood cells needed hydrogen peroxide to sense the wound, and move towards it." Of course, zebrafish are not people, and while our genomes share many similarities with these tiny fish, it isn't yet clear that natural selection has conserved this process throughout the evolutionary family tree. Still, these findings offer something of a conceptual shift in how to view human conditions where hydrogen peroxide plays a role. "When we look at how hydrogen peroxide works in people, this really starts getting intriguing," says Mitchison. In the human body, hydrogen peroxide is produced primarily in three places: lung, gut, and thyroid gland. Because hydrogen peroxide, and the proteins responsible for producing other ROS molecules, are especially present in lung and gut, the researchers hypothesize that human diseases relevant to these findings would include any in the lung and gut that involve disproportionate levels of white blood cells, like asthma, chronic pulmonary obstruction, and some inflammatory gut diseases. "Our lungs are supposed to be sterile; our guts are anything but," says Mitchison. "It's very logical that both those tissues produce hydrogen peroxide all the time. Perhaps in conditions like asthma, the lung epithelia is producing too much hydrogen peroxide because it's chronically irritated, which, if our findings translate to humans, would explain inappropriate levels of white blood cells. This is certainly a question worth pursuing." Mitchison is currently laying the groundwork for investigating this hypothesis. This research was funded by the National Institutes of Health. Journal reference:
Philipp Niethammer, Clemens Grabher, A. Thomas Look, Timothy J. Mitchison. A tissue-scale gradient of hydrogen peroxide mediates rapid wound detection in zebrafish. Nature, 2009; 459 (7247) DOI: 10.1038/nature08119
Adapted from materials provided by Harvard Medical School.
|
|
|
|
NEWS
Jun 4, 2009 17:16:19 GMT 4
Post by avid on Jun 4, 2009 17:16:19 GMT 4
I, myself, am not a fan of QuickTime - however - here is (are) the fix(es) for the latest wormy Apple stuff...I'm still waiting for the latest DirectX patches from MicroSnot... ;D edited for length ;D Thanks - sorted!!! 123realchange.blogspot.com/2009/06/project-expose-msm-reports.htmlWednesday, June 3, 2009
Project Expose MSM Reports
Newsweek & Michael Isikoff
As noted in the announcement, 123 Real Change invites all members of the National Security Whistleblowers Coalition, other active (covert or overt) government whistleblowers, and reporters, to publish their experiences in regard to their own first-hand dealings with the media, where their legit disclosures were either intentionally censored/blacked out, tainted, or otherwise met with a betrayal of trust.
Here is the first project report, this one based on my own first-hand documented experience. In 2003 Newsweek reporter Michael Isikoff interviewed me for, and then published a story on the FBI translation program. His report knowingly omitted crucial facts, directly relevant cases, witness statements and confirmed official reports, while advancing the FBI's already-discredited point of view...
The push for honesty in the media thank goodness - folk are 'coming out of the woodwork' at last! There is strength in numbers.   |
|
|
|
NEWS
Jun 4, 2009 17:30:01 GMT 4
Post by avid on Jun 4, 2009 17:30:01 GMT 4
|
|
|
|
NEWS
Jun 4, 2009 23:18:28 GMT 4
Post by towhom on Jun 4, 2009 23:18:28 GMT 4
Hiya avid! 
I hope you and yours are well and happy.
I use hydrogen peroxide (the 3% solution available everywhere) in place of chlorine bleach. It is great for cleaning and disinfects without the "toxic fumes and other hazards".
This same solution can be used as a topical rinse for wounds.
As far as internal usage, one needs the "food grade" or 35% hydrogen peroxide. CAUTION IS REQUIRED WHEN USING THIS. It is HIGHLY concentrated and needs to be handled and stored with extreme safety measures. In addition, I would not use this without first consulting with a medically trained person who has a background in its use. It must be diluted in small quantities and the remaining concentrate must be stored in a refrigerator in GLASS.
I will tell you that using the 3% solution for cuts, as an oral rinse (no swallowing), on bug bites, etc. has worked wonders. Those who have problems with periodontal disease should consider using it as a rinse daily and baking soda in the place of toothpaste. I dip my dental floss in the hydrogen peroxide before flossing, too, so the solution gets into the gum line. It has really made a impact on my teeth - so much so that my dentist even remarked on it.
Here is one of many links referencing H2O2 which lists the different grades and their general uses:
www.cancertutor.com/Cancer/HydrogenPeroxide.html
Hope this helps.
Peace and Joy
Always
Sally Anne 
PS - the MMS is a totally different supplement used to provide a large variety of minerals and trace elements the body requires. I use another proprietary compound, CellFood. I haven't check out MMS yet.
|
|
|
|
NEWS
Jun 5, 2009 4:54:43 GMT 4
Post by towhom on Jun 5, 2009 4:54:43 GMT 4
Scientists Demonstrate All-fiber Quantum LogicScienceDaily
June 4, 2009www.sciencedaily.com/releases/2009/05/090528135246.htmA team of physicists and engineers have demonstrated all-fiber quantum logic, where single photons are generated and used to perform the contolled-NOT quantum logic gate in optical fibers with high fidelity.The only quantum technology in practical use today is quantum cryptography and is currently limited in the distance over which secure communication may occur.[Note: snicker, snicker...duhhhh]More sophisticated quantum networks will require multiple nodes with the ability to implement small-scale quantum processing in order to increase the range of quantum communications. Such networks will rely on optical fiber links, making fiber-based photon generation and information processing of key technological importance.[Note: Now a partial truth emerges...Fiber optics - the network platforms and optical fiber links are already available. They've been frantically installing the "interconnectivity architecture" (aka the fiber optics lines and signal regeneration equipment stations/points) for decades. They've been bypassing the copper-wire lines whenever and wherever possible in today's "telephony routing environment". Why is the "copper wire" left in place...that's another "story.  ] ]Jeremy O’Brien, Professor of Physics and Electrical Engineering at Bristol University and colleagues, have shown it is possible for a high-fidelity fiber controlled-NOT gate to operate with fiber heralded single-photon sources. Professor O’Brien speaking about the research, said: “On the basis of a simple model we are able to conclude that imperfections are primarily due to the photon sources, meaning that the gate itself works with very high fidelity.” “Such all fiber quantum information processing will likely have important applications in future quantum networks.” All-fiber quantum information processing could be used in less mature quantum technologies such as computing, communication and advanced measurement, as well as in the fundamental science of quantum optics.[Note: Isn't THAT special...]The team reported its results in the March 2009 issue of Physical Review A (Vol 79, No 3). Journal reference:
Alex S. Clark, Jérémie Fulconis, John G. Rarity, William J. Wadsworth, and Jeremy L. O%u2018Brien. All-optical-fiber polarization-based quantum logic gate. Physical Review A, 2009; 79 (3): 030303 DOI: 10.1103/PhysRevA.79.030303
Adapted from materials provided by University of Bristol.
|
|
|
|
NEWS
Jun 5, 2009 5:08:03 GMT 4
Post by nodstar on Jun 5, 2009 5:08:03 GMT 4
Sally Anne ..
A PM awaits .. ;D
love
Nod
|
|
|
|
NEWS
Jun 5, 2009 5:35:08 GMT 4
Post by towhom on Jun 5, 2009 5:35:08 GMT 4
There's Never Enough Hate And Fear On Fox News - So Long As It's Directed At Their Preferred TargetsNews Hounds - We watch FOX so you don't have to.
Reported by Ellen - June 3, 2009www.newshounds.us/2009/06/03/theres_never_enough_hate_and_fear_on_fox_news_so_long_as_its_directed_at_their_preferred_targets.phpSean Hannity used the recent shooting outside a military recruiting station in Arkansas to ratchet up fear and hatred on his show last night (6/2/09). The targets were the usual scapegoats: liberals, Muslims, and Iran. Hannity made it a grand slam by tying it all in with President Obama via a suggestion – never verified – that the shooting proved that we're more vulnerable than ever to terrorism and that he's making us more so. Hannity was aided and abetted in that mission by his lone guest, the unhinged Islamophobe, Brigitte Gabriel. With video. Nothing Gabriel said indicated she knew anything about the case of Abdulhakim Mujahid Muhammad, an Islamic convert who shot two soldiers standing outside a military recruiting station Monday, other than that it served as fodder for another of her anti-Islamic screeds. Hannity began with a swipe at liberals and Obama: “So much was made by the president and Eric Holder when we had the killing of this abortion doctor (Dr. George Tiller),” Hannity started off resentfully. “And here we have somebody who's a recent convert, apparently. Do you believe this was a terrorist act?” he asked Gabriel. Of course she did. Not that she felt the need to offer any evidence, however, nor did Hannity ask for any. “This is a matter that we should be paying attention to,” Gabriel began, in her chronically hysterical voice. “Because Al Qaeda and different terrorist organizations are targeting specifically the inner cities in the United States.” Nice way to disguise the fact that she either knew nothing about the shooting or, more likely, had no specifics to tie it to Islamic terror. She went on to say that Al Qaeda is recruiting from the African American and Hispanic communities “and they are partnering, basically, with gangs... to help them commit terrorist attack in the United States, even on the individual level like what we witnessed today.” Hannity noted that prior to the shooting, Muhammad had been investigated by the FBI's terrorist task force. “To what extent are we infiltrating these extremist mosques that exist... here in America?” he asked. “We are infiltrating them,” Gabriel said. “And we have to give credit to President Bush for instituting such programs like the wiretapping program where we were able to find out where these terrorist cells are and monitor them.” But in case anyone might want to relax with the feeling of safety thanks to President Bush, the Lebanese-born Gabriel feverishly said, “We realize that there is SUCH (her emphases) terrorist infrastructure in the United States set up by DIFFERENT varieties of Muslim radical organizations, that may not all be Al Qaeda but they all share the same ideology and we know that MILLIONS of dollars is being funneled, basically, to these terrorist cells FROM the Middle East, helping them not only get radicalized but like in THIS CASE (sending them to Middle Eastern countries) and TRAINING THEM and making them become HARDENED individuals for specific operations in the United States.” Gabriel seemed to be suggesting that Muhammad's crime was part of some large terrorist plot. But if she had even a shred of evidence, it's hard to believe she would not have brought it forth. Hannity didn't ask for any, either. Also not provided nor asked for were any concrete examples of the kind of “specific (terrorist) operations in the United States” she alleged are going on. Instead, Hannity moved on to tar President Obama. Referring to Obama's upcoming speech in Cairo, Hannity asked peevishly, “Why do I expect that it's gonna be an extension of his apology tour?” He also complained about Obama saying that Iran “has a right to go nuclear.” According to the AP, what Obama said was, “What I do believe is that Iran has legitimate energy concerns, legitimate aspirations. On the other hand, the international community has a very real interest in preventing a nuclear arms race in the region." AP noted that his comments echo remarks Obama made in Prague last month in which he said his administration would "support Iran's right to peaceful nuclear energy with rigorous inspections" if Iran proves it is no longer a nuclear threat. Predictably, Gabriel did not correct Hannity but instead used his distortion as an opening for her own, overheated, fear mongering. “It's very CONCERNING what he is talking. He is sending all the wrong signal.” She claimed to have just read an article about Obama's interview that “he gave today in France.” Actually, he gave the interview to a French reporter while he was still in the United States (he goes to France on Saturday). “And he said AMERICA is one of the GRANDEST Muslim countries in the WORLD.” She was “just shocked that he would say something like that.” Actually, what Obama said was, “If you actually took the number of Muslims Americans, we'd be one of the largest Muslim countries in the world. And so there's got to be a better dialogue and a better understanding between the two peoples.” It's hard to see what's so shocking about that - unless you're a rabid Islamophobe. “Obviously he is PANDERING to the Muslim(s),” Gabriel screeched. “He is trying to win their approval. Meanwhile, he is appearing VERY weak which is giving a great signal to Iran.” Once again, no proof offered or asked for, as Gabriel went on to hypothesize and suggest as fact, “Why should Iran stop DEVELOPING a nuclear if, finally, they got America, and in this case the president, to say, 'You know, maybe we should be OK with them developing energy.'” Actually, Obama is correct. Under the Nuclear Non-proliferation Treaty, Iran has the “inalienable right” to pursue nuclear energy, according to the Council on Foreign Relations. The U.S. and other western countries accuse Iran of failing to abide by NPT safeguards, and of pursuing technology to produce nuclear weapons. Obama's statement about supporting Iran's nuclear energy was very clear that he would support Iran's nuclear energy so long as the rest of the world can be sure there will be no nuclear weapons. But neither “expert” Gabrielle nor host Hannity gave the audience that “balancing” information. So much for “we report, you decide.” “I expect that the president is probably going to just continue this apology tour.” Hannity whined. He griped that the president should, instead, be pointing out all the American sacrifices that have been made for Muslims (not that Hannity ever suited up and made any). “These are the points that President Obama needs to be PRESSING in his speeches to the Arabic world.” Gabriel dictated Obama must drive home all that America has done for them and to “protect them from their fellow Muslims, like in the case of Kuwait.” Hannity said that he'd also like Obama to “challenge moderate Muslims to stand up against extremists.” Gabriel agreed. She thought Obama should have said, "The moderate Muslims in the whole world should unite together to fight radicalism in their community.” It was very surprising, indeed, to hear her say that. Because just last August, Gabriel told the New York Times that moderate Muslims “at this point are truly irrelevant.” Meanwhile, Hannity completely ignored the signs of militia-movement type terrorism in the shooting of Dr. Tiller. The suspect, Scott Roeder, had a history of extremism and had been previously arrested and charged with having bomb-making equipment. If they were really fair and balanced, Fox would have pointed out that the incident may have validated the much- maligned- on- Fox report of the Department of Homeland Security about the rise of right-wing extremism. A truly fair and balanced presentation would have considered extremism and terrorism as a whole, from the vastly different perspectives. One gets the sense that maybe they just don't care about right-wing extremism on Fox... unless they can blame it on Obama or liberals.
|
|
|
|
NEWS
Jun 5, 2009 6:51:26 GMT 4
Post by towhom on Jun 5, 2009 6:51:26 GMT 4
Why you need to validate your downloads Windows Secrets
By Ian "Gizmo" Richards
2009-06-04 One of the most common ways of getting a malware infection is by downloading and installing a seemingly legitimate program that has actually been tampered with. You can seriously reduce the risk of this kind of infection by using a free checksum program that makes it easy to validate files before you open them. Using checksums to validate downloadable files The idea of using a checksum calculated from a set of data to validate the accuracy of that data is not restricted to file downloading; it is commonplace. Take, for example, your credit card. Whenever you give someone your credit card number, it's important that they get it exactly right. However, there's always a chance that you or the person recording your card number will make a mistake. To guard against these transcription errors, credit card companies have built in a simple checking mechanism to ensure the validity of the card number. The last number on your credit card is not part of your account number but is a check digit. If you apply a standard formula to all the other numbers on the card, you should end up with a number corresponding to the check digit. If you don't, something is wrong. An example of such a formula would be to add up all the numbers on the card and then compare the last digit of the result to the check digit. So if your numbers added up to 72, the check digit should be 2. In practice, the formula used for credit cards — called the Luhn algorithm — is a little more complex, but the idea is the same. The Luhn algorithm is just one example of a checksum algorithm. However, it shares a weakness with other simple checksum methods: it can certainly detect incorrect digits but can't detect a lot of other common errors, such as the simple transposition of two digits. To do that, a more complex method is needed. The Cyclic Redundancy Code (CRC) technique is the next step up in error detection. CRC can detect not only incorrect digits but also digits out of sequence. There are many CRC algorithms, but the most common is CRC32. Even CRC32 has a weakness: while it's excellent at detecting accidental errors, it's not robust against deliberate falsification. In other words, it's possible for a knowledgeable attacker to modify the data yet ensure that it generates the correct checksum. To guard against this, we need even more sophisticated methods. These more advanced techniques are usually called cryptographic hashes rather than checksums. The most common of these cryptographic hashes is Message Digest number 5 (MD5), which is capable of producing a 128-bit fingerprint. MD5 is more difficult to falsify by reverse engineering than CRC32. However, even MD5 is no longer considered fully secure. A smart hacker can tamper with the file in such a way that it still gives a valid checksum. MD5 is good enough for casual file verification purposes, but there's a strong move to more-secure hashes, such as the Secure Hash Algorithm (SHA-1) and RACE Integrity Primitives Evaluation Message Digest (RIPEMD, which has evolved into RIPEMD-160 and other, more-recent variants). RACE stands for "R&D in Advanced Communications Technologies in Europe." Ah, we techies do love our embedded acronyms! Whatever the technique, the idea is still much the same as the check digit on a credit card. You run a program that calculates a number — the hash — from the data and compare this to the correct hash quoted for that data by the publisher or download site. If the two don't agree, you have a problem. Why hashes matter when you download a file Just as it's important to get your credit card number right when making a transaction, you need to validate the programs you download before opening them. And believe me, downloads can get corrupted. By far the most common cause is an error in transmission, usually as a result of a download that didn't fully complete. However, even files that appear to download completely can still be corrupted accidentally. But corruption can also be deliberate. A hacker may have modified the original file and secretly inserted a Trojan or other malware program. This is not uncommon for files distributed via BitTorrent or other file-sharing services. (I wrote in my Jan. 15 column that 39 out of 61 illegal programs I tested after downloading them using BitTorrent were infected.) The use of an MD5, SHA-1, or other hash will detect corruption, whether accidental or deliberate. That's why you should validate all downloads against the checksums or hashes provided by the program distributor. Unfortunately, not all download sites provide these hashes, but if they do, be sure to use them. Thankfully, there are some excellent free programs that simplify the task of calculating hashes for your downloaded files. I looked at seven different free checksum and hashing utilities and describe in today's column the three I consider the best for typical PC users. If you want to calculate only the common hashes, such as MD5 or SHA-1, any of these programs will do the job — though they differ in usage and the types of hashes they calculate. #1: WINHASHER 1.03File checker runs from .exe without installer If you download files only occasionally, you may be attracted to WinHasher 1.03, mainly because the program runs directly from the .exe file without installing. However, WinHasher does require the Microsoft .NET Framework 2.0. To use WinHasher, you must first select the hash method you want from a list of eight different hashing algorithms, several of which have iterations of their own. (See Figure 1.) Then you select the file you want to analyze. WinHasher calculates the hash and can also compare it to the hash published by the download site. WinHasher also generates or validates hash files, if required. 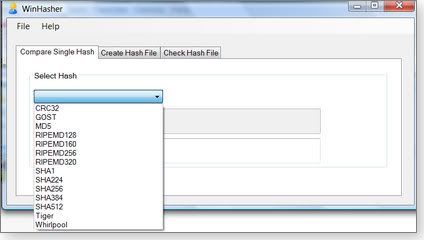 Figure 1. The WinHasher file validator supports eight different hashing algorithms. Figure 1. The WinHasher file validator supports eight different hashing algorithms.The most-recent version, WinHasher 1.4, includes more features, such as the ability to create hashes from the right-click (context) menu and to generate hashes from text. However, this version requires installation. Personally, I prefer the earlier version because it's portable. If you're fine with a program that needs to be installed, however, I suggest you look at either FileTweak or HashCalc, both of which are described below. Download version 1.03 (334KB) from Download.com or version 1.4 (374KB) from the vendor's site. #2: FEBOOTI FILETWEAK HASH & CRC 2.0Check downloaded files via Properties dialog The name "Febooti FileTweak Hash & CRC" might be a mouthful, but this product is delightfully simple to use. Once installed, the program adds a Hash & CRC tab to the file's Properties dialog — the one that opens when you right-click the file and choose Properties. FileTweak handles all the formats shown in Figure 2, plus RIPEMD-128, -256, and -320. However, the program can't compare calculated hashes with published values; you'll need to do that manually. 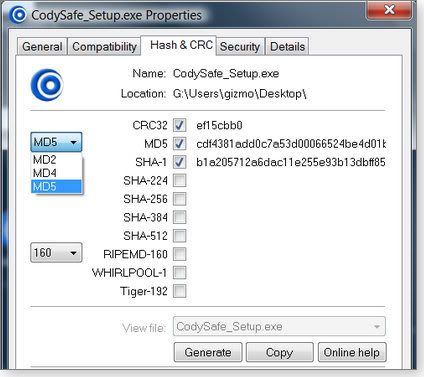 Figure 2. FileTweak adds a file-checker option to the file's Properties dialog in Windows. Figure 2. FileTweak adds a file-checker option to the file's Properties dialog in Windows.Download FileTweak from the vendor's site (264KB). #3: SLAVASOFT HASHCALC 2.02The drag-and-drop way to check your downloadsSlavaSoft's HashCalc runs as a standalone application, so once it's running, you simply select the file you want to check and the hashing method to use, and then click Calculate. Alternatively, you can drag and drop the file into the program window. HashCalc handles 13 different checksum and hashing algorithms, including the special method used by the eDonkey/eMule file-sharing services. 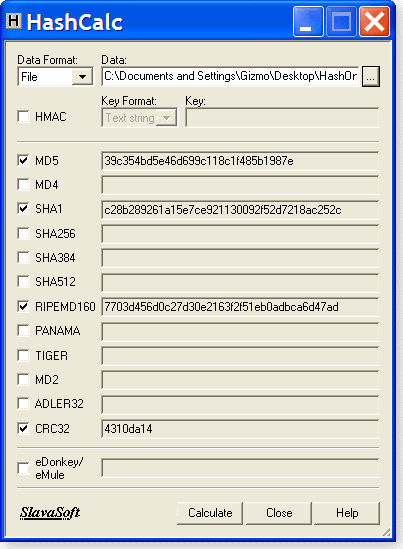 Figure 3. HashCalc supports keyed-Hash Message Authentication Code hashes for an added level of security. Figure 3. HashCalc supports keyed-Hash Message Authentication Code hashes for an added level of security.This program processes not only files but also text or hex strings. It's also the only program of the three described here that can process keyed-Hash Message Authentication Code (HMAC) hashes. HMAC combines a hash with a key and is typically used in high-security environments. HashCalc is available from the SlavaSoft site (468KB). So which is my favorite download verifier? I like WinHasher 1.03 because it's portable and is the only product in this group that checks the generated hash against the published hash. However, the choice is ultimately a matter of personal preference. I suggest you try all three, as they're tiny programs that can be downloaded in a few seconds. But please do get yourself a hash-checking program. There are simply too many dodgy downloads floating around the Internet to risk accidentally downloading a file that has been tampered with. Make sure, though, to get your published hashes or checksums from the original source of the program rather than get some untrustworthy value obtained from a file-sharing service.
|
|
|
|
NEWS
Jun 5, 2009 7:05:23 GMT 4
Post by towhom on Jun 5, 2009 7:05:23 GMT 4
Yes or no to firewall request to act as server? Windows Secrets
By Fred Langa
2009-06-04 It's not always easy to tell whether a program really needs the rights and privileges of a server. When your firewall alerts you that an application wants to act as a server, you have two simple ways to determine the correct response. Find out why a program wants server status Maurice Carson ran into one of those all-too-common, half-explained firewall queries: - "What about programs wanting to 'act as a server'? I have ZoneAlarm as a firewall, and many programs want to act as a server. Why?"
First, let's define the jargon. A "server" is a program that responds to a request from another program to open a connection, send or receive a file or data, launch a program, or perform some other task. A "client" is a program that makes such a request. Technically, client and server programs can reside on the same machine. Security risks come into play when the client and server are on separate networked machines. Some programs are both clients and servers, while others — known as "standalone applications" — are neither. ZoneAlarm and other security tools are especially suspicious of any program that wants to act as a server, because letting other PCs request data or services from your system is obviously risky. The firewall has no way of knowing whether the request to act as a server is legitimate, so it punts the decision to a human — you. The simple, empirical way to respond to a program's request to act as a server is to choose the "No" or "Deny" option (or whatever verbiage your security tool uses) every time. Denying the request is always safest; you'll never reduce your security by blocking a program's request for server rights.Saying no may cause some necessary features or functions of the program to stop working, however. In these cases, the application really does need to act as a server. You can then adjust your security tool's settings accordingly. The "default to No" method is crude but effective. I prefer to figure out why a particular program might need to respond to a client's request for a file or other resource. For example, it's pretty clear that the Skype voice-over-IP (VoIP) tool needs to act as a server in order to respond to incoming phone calls. Likewise, if you use a file-sharing app that makes your PC part of a network for receiving and redistributing files, acting as a server is part of the deal.In cases like these, you'd let the software in question act as a server. But keep in mind that it's always more dangerous to allow server requests. Doing so opens a path into your PC for outside service requests. Of course, this may be necessary for the software to work as intended. If you don't recognize the would-be server program or don't understand why it's making a request to act as a server, do a little research. If possible, query a search engine with the exact wording of the relevant part of your security tool's message, and include the name of the program making the server request. Odds are many other people have asked about the same program and the answer is just a few clicks away. If you can't find an answer online, fall back to the empirical method. Or, as I'd put it more simply: "When in doubt, lock it out, but if it breaks, raise the gates!"
|
|



 ]
]

